Cybersecurity is defined as the collection of methods, technologies, and processes used to protect the confidentiality, integrity, and availability of computer systems, networks, and data from cyber-attacks or unauthorised access. The primary goal of cyber security is to protect all organisational assets from both external and internal threats, as well as natural disaster disruptions.
Because organisational assets are comprised of numerous disparate systems, an effective and efficient cyber security posture necessitates coordinated efforts across all of their information systems.
What does NIST Cybersecurity Framework do?
The NIST cybersecurity framework is a valuable resource for organising and improving your cybersecurity programme. It is a set of guidelines and best practices designed to assist organisations in developing and improving their cybersecurity posture. The framework suggests a set of recommendations and standards to help organisations better prepare for identifying and detecting cyber-attacks, as well as guidelines for responding to, preventing, and recovering from cyber incidents.
This framework, developed by the National Institute of Standards and Technology (NIST cybersecurity framework), addresses the lack of standards in cybersecurity by providing a consistent set of rules, guidelines, and standards for organisations to use across industries. The National Institute of Standards and Technology NIST Cybersecurity Framework (NIST CSF) is widely regarded as the gold standard for developing a cybersecurity programme. Whether you’re just getting started with a cybersecurity programme or you already have one in place, the framework can add value by serving as a top-level security management tool that helps assess cybersecurity risk across the organisation.
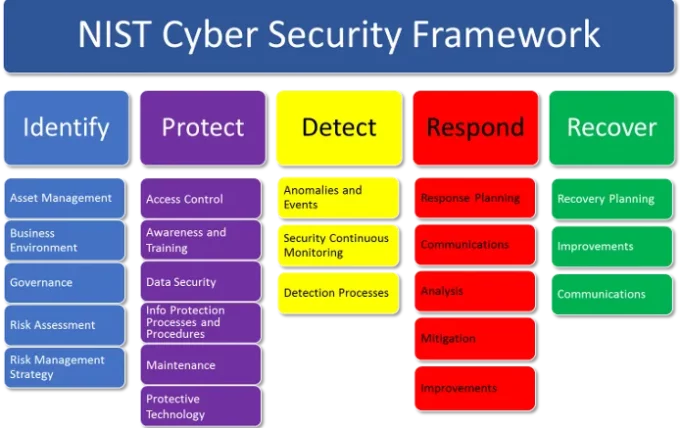
The NIST Cybersecurity Framework 5 Core Functions
IDENTIFY
The Identify function is responsible for laying the groundwork for a successful cybersecurity programme. This function contributes to the development of an organisational understanding of cybersecurity risk to systems, people, assets, data, and capabilities. This function emphasised the importance of understanding the business context, the resources that support critical functions, and the associated cybersecurity risks in order to enable an organisation to focus and prioritise its efforts in accordance with its risk management strategy and business needs. This group’s essential activities include:
- Identifying physical and software assets as the foundation for an asset management programme
- Identifying the business environment of the organisation, including its role in the supply chain
- Identifying established cybersecurity policies to define the governance programme, as well as legal and regulatory requirements regarding the organization’s cybersecurity capabilities
- To assess risk, we identify asset vulnerabilities, threats to internal and external organisational resources, and risk response activities.
- Developing a risk management strategy, which includes determining risk tolerance
- Developing a supply chain risk management strategy that includes priorities, constraints, risk tolerances, and assumptions used to support risk decisions related to supply chain risk management is challenging.
PROTECT
The Protect function outlines appropriate safeguards to ensure critical infrastructure services are delivered and supports the ability to limit or contain the impact of a potential cybersecurity event. This group’s critical activities include:
- Implementing identity management and access control safeguards within the organisation, including physical and remote access,
- Staff empowerment through security awareness training, which includes role-based and privileged user training,
- Creating data security safeguards that are in line with the organization’s risk management strategy to protect the confidentiality, integrity, and availability of information.
- Implementing processes and procedures to maintain and manage the security of information systems and assets
- maintaining organisational resources, including remote maintenance activities.
- technology management to ensure system security and resilience in accordance with organisational policies, procedures, and agreements.
DETECT
It is critical to detect potential cybersecurity incidents, and this function defines the appropriate activities to detect the occurrence of a cybersecurity event in a timely manner. This function’s activities include:
- Making certain that anomalies and events are detected and that their potential impact is understood.
- Continuous monitoring is being set up to keep an eye on cybersecurity events and make sure that protective measures, like network and physical activities, are working.
- The Respond function focuses on appropriate activities to take action in the event of a detected cybersecurity incident and helps to limit the impact of a potential cybersecurity incident. This function’s essential activities include:
- Ensuring that the response planning process is followed both during and after an incident
- Managing internal and external stakeholder communications during and after an event
- Analyzing the incident to ensure an effective response and supporting recovery activities such as forensic analysis and incident impact
- Executing mitigation activities to prevent an event from spreading and to resolve the incident
- Detection and response activities can be made better by using what we’ve learned from past and current activities.
RECOVER
The Recover function identifies appropriate activities to renew and maintain resilience plans, as well as to restore any capabilities or services that have been compromised as a result of a cybersecurity incident. To mitigate the impact of a cybersecurity incident, it is imperative that normal operations resume as soon as possible. This function’s essential activities somewhat overlap with those of Respond and include:
- Ensure that the organisation has recovery planning processes and procedures in place to restore systems and/or assets affected by cybersecurity incidents.
- Improving existing strategies and implementing improvements based on lessons learned
- Internal and external communications are coordinated during and after a cybersecurity incident.
What are the benefits of using the NIST Cybersecurity Framework?
First, let’s take a step back and go over some of the most pressing cybersecurity concerns.
- You are concerned about unknown risks and vulnerabilities.
- You do not have an accurate inventory of assets that must be safeguarded.
- Your team spends a lot of time on things that won’t make a difference, but you’d rather they focus on real risks.
- You want to know how to deal with risky items given your current tools and what’s on the market.
- Your coworkers who aren’t on the security team don’t know much about cyber risk, so they don’t “own” important tasks for reducing it.
- Your board has begun to inquire about quantifying the risk reduction outcomes of the strategic cybersecurity plan that your team has been implementing. “Are we NIST compliant?”
The framework can assist you in dealing with these difficulties. You will be able to learn from how other people have dealt with similar problems in the past.
The framework’s goal is to assist you in prioritising cybersecurity investments and decisions. The framework also helps you figure out how mature your programme is and gives you a way to talk about it with people like your senior management and board of directors.
How to Begin Using the NIST Cybersecurity Framework
Aligning with the framework entails listing all of your activities and labelling them with one of the five function labels. The Identify label, for example, will be for tools that help you inventory your assets. Firewalls and Crowdstrike will be included in Protect. However, depending on their capabilities, they would be placed in Detect alongside your IDS and SIEM. Respond contains your incident response tools and playbooks. Recover includes backup and recovery tools.
After completing this exercise, some of your buckets may feel more empty than others, and you may be uneasy about the corresponding function description in the image above. That’s great; you can now articulate what your cybersecurity programme is lacking.
Where Can I Find the Best Network Security Tools in 2022?
There are numerous open-source and paid network tools available on the market that you can use to strengthen your networking security. The top 12 cyber security tools for 2022 are listed below.
#1. Kali Linux
It is one of the most effective penetration testing tools for scanning IT systems and networks for vulnerabilities. This cybersecurity tool includes approximately 300 different pieces of software used for security auditing. Because the majority of these tools are executable, users can monitor and maintain their network security systems with a single click. The most common feature of Kali Linux is that it can be used by all types of users, from experienced to inexperienced, to strengthen their networking security. It does not require a specific set of skills or a degree to function.
#2. Wireshark
Wireshark, formerly known as Ethereal, is open-source network software that can analyse network protocols and improve security in real time. You can use this security software to sniff the network and monitor your network traffic in real time because it is a console-based password auditing and packet sniffing tool. Security experts use this powerful software to capture data packets and look at the features that each data packet has. This helps them find security flaws in a network.
#3. Metasploit
Metasploit is a great piece of security software that includes a variety of tools for performing penetration testing services. Professionals use this tool to achieve a variety of security goals, including identifying system vulnerabilities, strengthening computer system security, weaving cyber defence strategies, and maintaining complete security assessments. These penetration testing tools can examine various security systems, such as web-based apps, servers, and networks. Metasploit can find all new security holes as soon as they appear. This makes sure that top-level security is always in place.
#4. John the Ripper
Professionals use John the Ripper to test the strength of passwords. This tool can quickly search for complex cyphers, encrypted logins, and hash-type passwords, as well as identify weak passwords, which can pose a significant risk to a protected system. The software is compatible with Windows, DOS, OpenVMS, and Unix environments.
#5. TCPDUMP
Tcpdump is one of the most effective packet sniffer security tools for monitoring and logging TCP/IP traffic over a network. It is a command-based tool that makes it easy to define network security and the contents of system traffic packets.
#6. Cain and Abel
It is a network security tool that audits passwords and sniffs packets to find flaws in Windows operating systems. IT professionals rely on this software to improve networking security and identify flaws in the Windows security password. You can use this free tool to identify password flaws and recover them. Cain and Abel has a plethora of features, including the ability to record VoIP communications, analyse routing protocols, decode scrambled passwords, crack encrypted passwords, and so on. This software is also very effective at cryptanalysis. Consider using this security tool as a good starting point for all types of packet sniffing exercises.
#7. Forcepoint
Forcepoint is a customizable security tool aimed primarily at cloud users. The tool is used to define network security, prevent users from accessing specific content, and detect and prevent various intrusion attempts. Security administrators can configure Forcepoint’s SD-Wan to monitor and detect suspicious activity in a network quickly and implement appropriate action. The tool provides an additional layer of defence against more serious threats.
#8. NIKTO
Nikto is open-source security software that detects web vulnerabilities and takes appropriate action. The software includes a database with over 6,400 different threats. Security professionals keep this database up to date so that users can easily identify new vulnerabilities.
#9. Nmap
Nmap, also known as Network Mapper, is a free network discovery and security auditing tool that professionals use to scan both single hosts and large networks. Its key features include the detection of unknown devices and the identification of network issues for testing security vulnerabilities.
#10. Paros Proxy
Paros Proxy is a Java-based security tool that includes a number of additional tools such as vulnerability scanners, traffic recorders, web spiders, and so on. Professionals use these tools to scan security tests to find holes in the web and keep track of network activity in real time.
#11. Nexpose
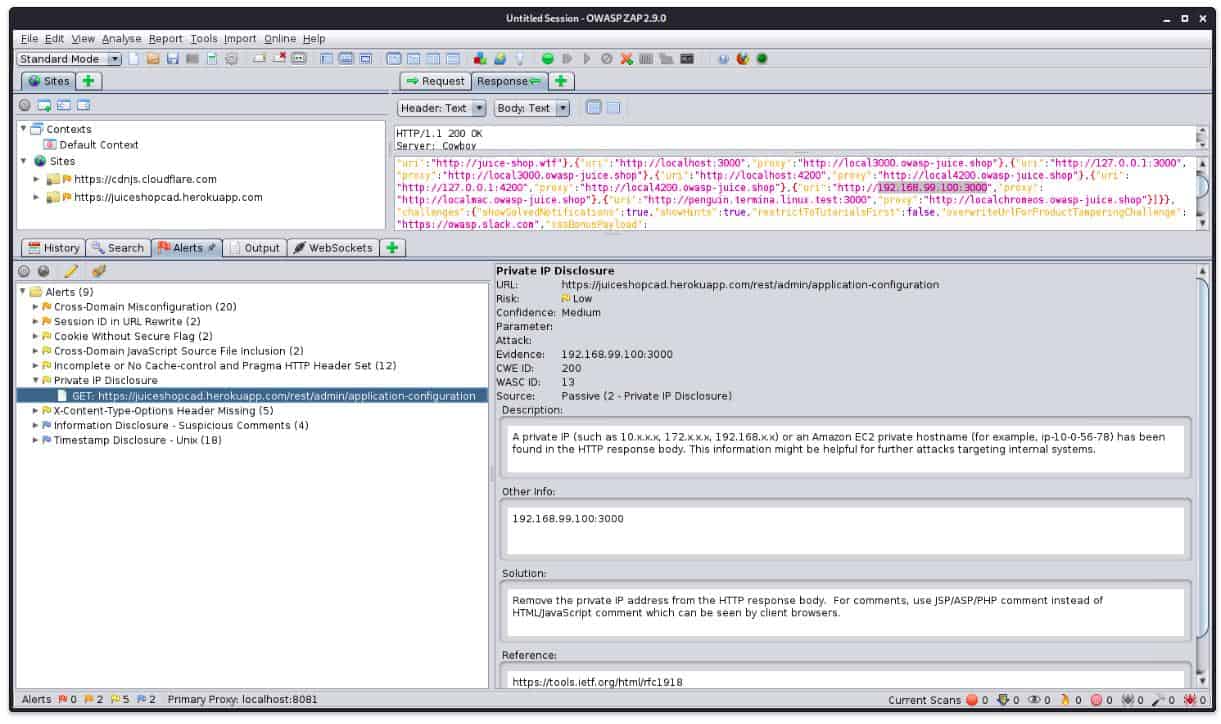
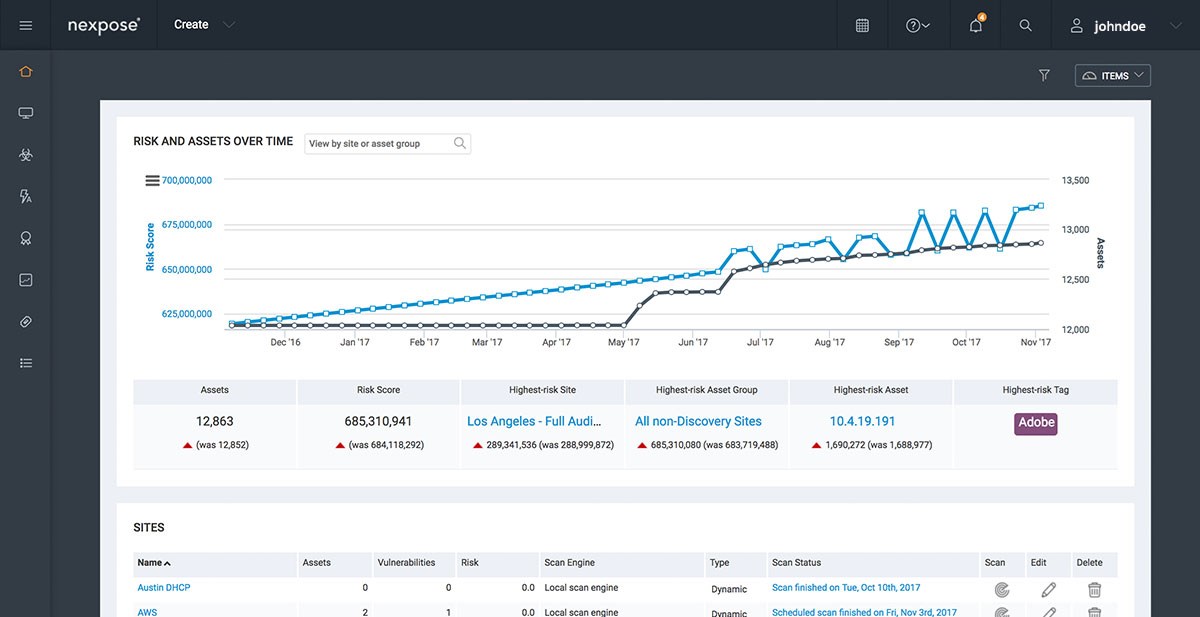
Nexpose is a user-friendly network security software that provides real-time capabilities for detecting vulnerabilities and reducing potential weak points on a network. Nexpose also lets users give vulnerabilities they find a risk score, which lets them be put in order of how serious they are.
#12. Nessus Professional
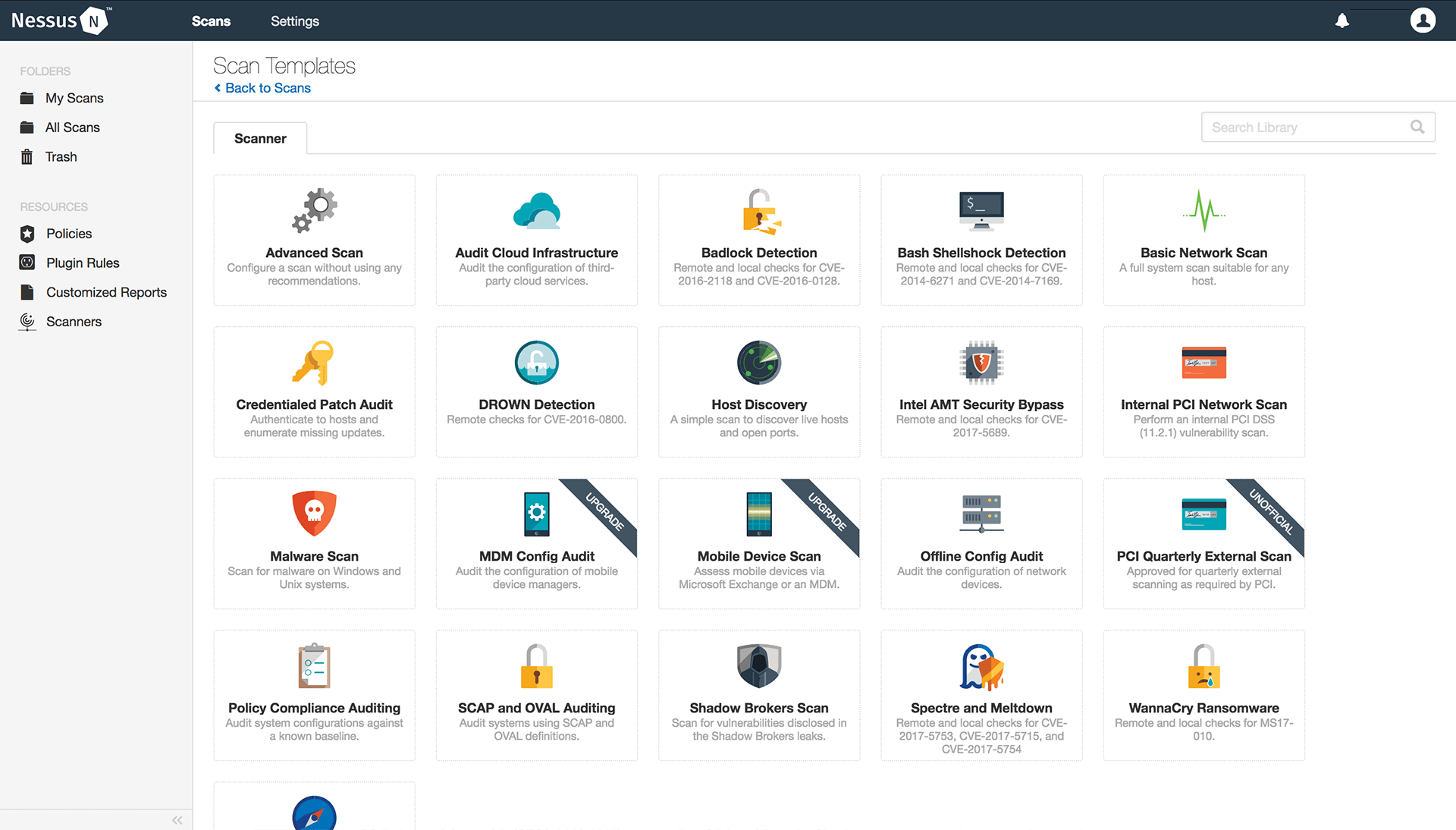
Nessus Professional is a powerful network software that can be used to define network security, correct system security flaws, and improve network integrity. The tool makes it easy to find and fix security flaws like wrong patches, software bugs, and general security misconfigurations in software, IT devices, and operating systems.
FAQS
What are the NIST cybersecurity framework’s five components?
The framework groups all cybersecurity capabilities, projects, processes, and daily tasks into these five core functions:
- IDENTIFY
- PROTECT
- DETECT
- RESPOND
- RECOVER
What does the acronym NIST stand for in the NIST cybersecurity framework?
NIST is an abbreviation for the National Institute of Standards and Technology, which is part of the US Department of Commerce.
The goal of the National Institute of Standards and Technology (NIST) is to improve the economic security and quality of life in the United States by making progress in measurement science, standards, and technology.