EDR security service is a way to keep track of online threats and respond to them in real time. Agents are deployed on the endpoints to gather and transmit behavioral data to a central database for analysis.
Patterns are later established and abnormalities are recognized using analytics technologies. Many Companies and Vendors Offering Endpoint Detection and Response EDR Security Services in 2022 Are Listed Below:
What is EDR?
Endpoint detection and response (EDR), also called endpoint detection and threat response (EDTR), is a type of endpoint security system that keeps an eye out for cyber threats like ransomware and malware on end-user devices.
According to Anton Chuvakin of Gartner, a solution that “records and stores endpoint-system-level behaviours, uses various data analytics techniques to find suspicious system behaviours, provides contextual information, blocks malicious activity, and suggests ways to fix affected systems,” is considered to be an EDR.
What is the process of endpoint detection and response?
Endpoint events are continually monitored. The tool stores data in a central database. After that, the data is evaluated and an inquiry is carried out. This inquiry will be used to inform reporting and changes. A software agent will be installed on the host machine. This software agent monitors and reports on events.
According to Gartner data, the EDR market has more than quadrupled in one year, with 60% of enterprises switching from on-premises EPP to managed endpoint security services.
Static AI is used in this endpoint detection and response solution, which eliminates the need for periodic scans. The use of a conventional signature has been supplanted by this technology. Every EDR service operates differently and has distinct capabilities.
Endpoint detection and response services are designed to do continuous monitoring and analysis in order to identify, detect, and prevent advanced threats. EDR security is a technology used to detect and evaluate unusual endpoint activity. This new technology is capable of detecting and responding to sophisticated threats.
Also Check: IoT Security Challenges, Solutions for Securing IoT Devices
EDR Security Services List
The top endpoint security companies on the market are mentioned below.
#1. CrowdStrike
CrowdStrike’s Falcon platform For Edr Security is adaptable and extendable. It offers a number of modules based on the Falcon platform, such as Falcon Prevent, Falcon Insight, Falcon Discover, and so on. CrowdStrike provides Falcon Pro, Falcon Enterprise, Falcon Premium, and Falcon Complete products.
Features:
- Falcon Enterprise will provide threat-hunting
- management and threat intelligence integration.
- Endpoint protection as a service is provided by Falcon Complete.
- Falcon Premium will provide you with complete endpoint security as well as increased visibility.
- Falcon Pro is designed for integrated threat intelligence and rapid reaction.
- Big data and artificial intelligence are used to power the Threat Graph.
#2. Carbon Black
Carbon Black offers solutions for virtualized data centre security, malware and non-malware protection, risk and compliance, ransomware prevention, and anti-virus protection. It may be installed on-premises or as a SaaS service. It is capable of analysing the attacker’s behaviour pattern.
Features:
- Even if an endpoint is down, it will still deliver the whole activity record.
- Its solution isolates affected systems and eliminates harmful files.
- Endpoint inquiry and remediation in real-time.
- This platform will give you next-generation anti-virus protection with EDR capabilities.
#3. Cynet
Cynet offers Endpoint Detection & Response as part of a comprehensive platform that safeguards the complete internal environment, including hosts, networks, data, and users. As a result, Cynet can give the whole environment awareness rather than just endpoint visibility, as well as prevent and identify attacks that other EDR security systems cannot.
It also features the most comprehensive collection of remediation capabilities, not just for endpoints but also for users and network traffic. The platform can be set up in hours and includes an extremely simple administration panel.
Cynet also has a free security team that works around the clock to keep an eye on customer environments, warn of dangers, look for threats before they happen, and help with responding to incidents.
Features:
- Within 2 hours, hundreds of endpoints were deployed.
- Total visibility of the environment, including hosts, files, networks, and users.
- preventing and detecting a wide variety of dangers at all phases of an assault.
- Each alert is shown in full, and you can easily zoom in to get a sense of how big the attack is.
- The most comprehensive suite of remediation tools for hosts, users, files, and networks.
- Response orchestration: customers can create unique remediation rules.
- The security staff at CyOps works 24/7 to warn clients, look for threats, and help with responding to incidents at no extra cost.
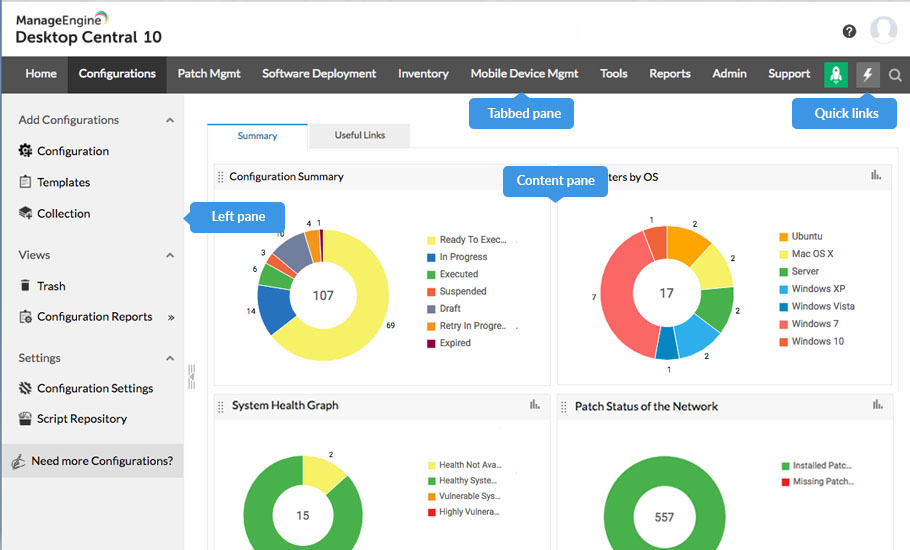
#4. ManageEngine Desktop Central
ManageEngine Desktop Central is a single solution for managing and protecting all endpoints over their entire life cycle.
Desktop Central has security add-ons like Vulnerability Manager Plus, Browser Security Plus, Application Control Plus, and Device Control Plus that make it possible to protect and secure every endpoint.
- Security add-on solutions aid in the protection of endpoints like desktops, laptops, and tablets in order to prevent cyberattacks from entering the corporate network.
- The agent on the endpoints collects and sends information to the central server about missing patches, security holes, the general health of the system, and other things.
- There are dashboards that make it easier to see missing patches, zero-day vulnerabilities, failed patches, graphs of system health, and other information.
- It makes it easy for administrators to handle things like setting up policies for all network systems, blocking access to certain websites, applying security protocols, patching holes, and so on for all endpoints.
#5. Symantec EDR
For all endpoints, Symantec EDR security can identify, isolate, and remove infiltration. This is accomplished through the application of artificial intelligence. It hunts threats around the clock. It will allow you to design your own research flow. Without the need for complicated scripting, you will be able to automate repetitive manual processes.
Features:
- Behavioural policies can identify advanced threats. These policies are constantly updated by Symantec researchers.
- It offers interconnected protection at the device, app, and network levels.
- There will be no complications because it uses a single agent and console.
#6. SentinelOne
SentinelOne protects against a variety of attack types. It will function by utilising a static AI engine, which will provide you with pre-execution safety.
SentinelOne’s behavioural AI engine can follow all processes and their interrelationships even if they have been running for a long time. Endpoints will be protected against a variety of assaults.
Features:
- It is capable of detecting threats at all levels.
- It will then undertake a thorough file examination.
- It will safeguard against ransomware assaults.
- It has a mild and all-encompassing agent.
- It has automated EDR security, which means that risks are automatically taken care of, networks are automatically cut off, and endpoints are automatically protected against new threats.
#7. Palo Alto Networks XDR
XDR is a threat detection and response technology. It will protect the infrastructure of a company. It will also safeguard data against damage, unwanted access, and abuse. XDR services are provided by Palo Alto Networks. It analyses network, endpoint, and cloud data to detect threats automatically.
Features:
- It does root cause analysis automatically.
- It is capable of containing and coordinating responses to any danger.
- It includes Cortex Data Lake, which can store massive amounts of data for months at a time. It will aid in the inquiry.
#8. Cybereason
Cybereason offers complete cybersecurity solutions. It offers threat monitoring and incident response services around the clock. The deployment will take 24 hours.
Features:
- Sensors on each endpoint will monitor the entire surroundings. The regulation will not need to be written.
- It functions more intelligently by remembering, relating, and linking previous and present events.
- Machine learning is used by the hunting engine. Machine learning will assist it in recognising the behaviour.
- It has a one-of-a-kind hunting approach, which is a custom-built in-memory graph. This approach queries each endpoint at a rate of 8 million queries per second.
#9. FireEye HX
Endpoint protection from FireEye is more secure than anti-virus security. The FireEye platform can respond on a large scale. It provides a wide range of detection and preventive capabilities. It combines critical security measures into a single agent.
Features:
- MalwareGuard, a machine learning-based protection engine, has been integrated.
- It will allow you to collect information on any action.
- Based on real-time facts, the analyst will react with knowledgeable and targeted replies.
#10. Cisco AMP
Cisco AMP (Advanced Malware Protection) offers endpoint protection services. It employs a number of anti-malware technologies for scanning files. It includes the Cisco antivirus engine. It will constantly monitor every file on the network.
Features:
- Based on the context-rich knowledge base, it can guard against known and upcoming threats.
- Using powerful sandboxing features, it can do automatic static and dynamic examinations of files.
- It contains antivirus detection engines that can detect and stop malware in real-time.
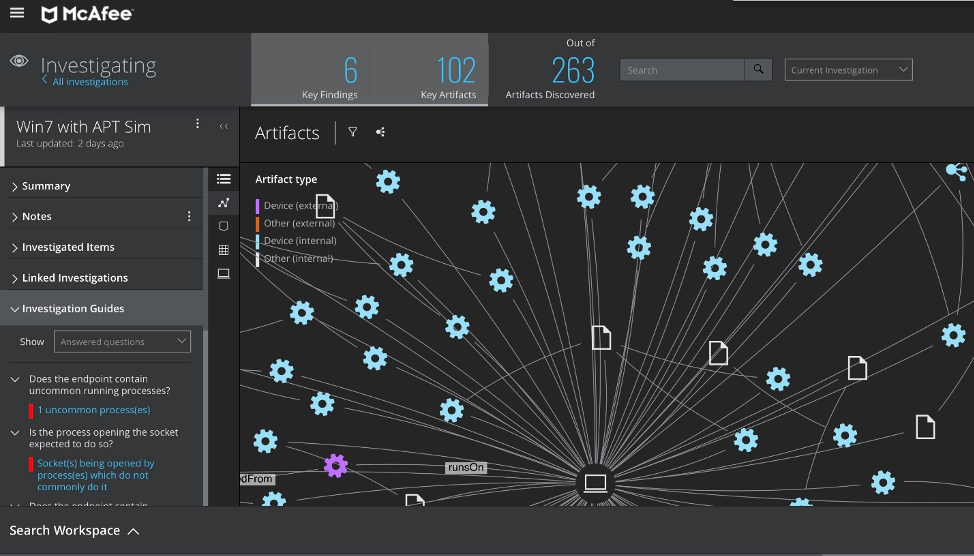
#11. McAfee EDR
McAfee delivers a cloud-based solution that is low-maintenance. It keeps an eye on endpoint activity in real-time. It offers cloud-based deployment as well as analytics.
Features:
- Key findings are automatically identified. There is no need for manual assessment.
- Based on the visuals that depict relationships, analysts will be able to grasp them rapidly.
- McAfee employs AI in its investigations.
Conclusion
This article is all about the best EDR Security services. As we’ve seen, Cynet offers a completely integrated endpoint security solution. It will help you manage vulnerabilities, deception, network analysis, threat intelligence, analytics, and threat intelligence.
CrowdStrike Falcon is a cloud-based endpoint security product. It includes capabilities like malware and exploits detection, security threat alerts, real-time system and application inventory, and so on.
Carbon Black offers a cutting-edge, cloud-based endpoint security solution. It is capable of analysing massive amounts of data. SentinelOne offers endpoint security to companies in a variety of areas, including healthcare, banking, education, and energy. Symantec EDR services will make investigation and threat hunting easier.
FAQ’s
What is a security EDR?
Endpoint Detection and Reaction (EDR) is a tiered method of endpoint protection that includes real-time continuous monitoring, endpoint data analytics, and rule-based automated response.
What exactly is EDR, and how does it work?
Endpoint detection and response (EDR) is a system that gathers and analyses information about security threats from computer workstations and other endpoints. The goal of EDR is to find security breaches as they happen and react quickly to threats that are found or suspected.
What is the difference between EDR and SIEM?
The basic purpose of a SIEM solution is to deliver actionable security information and event log gathering. On a single platform, all security intelligence from all sources is available. EDR’s main goal is to find ransomware, file-less attacks, and malware at the endpoint level and deal with them.
What is the difference between EDR and antivirus?
What Is the Difference Between EDR and Antivirus? AV software can identify and respond to malware on an infected machine using a variety of methods. EDR brings together antivirus and other endpoint security features to protect against a wider range of possible threats.